Configuring NiFi for SSO
Table of Contents
Goal¶
Integrate NiFi with an SSO provider to streamline authentication and rbac
Implementation Options¶
It is possible to use both SAML and OIDC for SSO; however, OIDC would be the preferred solution due to the ease of integration with Keycloak.
For additional information on SAML authentication see the following:
OIDC Integration¶
Given we are using the helm-nifi chart, the OIDC configuration must be compliant with the opinionated deployment.
The following configuration options must be specified in the values.yaml
| Oidc authentication | ||
|---|---|---|
auth.oidc.enabled |
Enable User auth via oidc | false |
auth.oidc.discoveryUrl |
oidc discover url | https://<provider>/.well-known/openid-configuration |
auth.oidc.clientId |
oidc clientId | nil |
auth.oidc.clientSecret |
oidc clientSecret | nil |
auth.oidc.claimIdentifyingUser |
oidc claimIdentifyingUser | email |
auth.oidc.admin |
Default OIDC admin identity | [email protected] |
| Note that OIDC authentication to a multi-NiFi-node cluster requires Ingress sticky sessions | See background | Also how |
Example values.yaml
auth:
oidc:
enabled: false
discoveryUrl: https://keycloak.cybernetics.home.lab/auth/realms/homelab/.well-known/openid-configuration
clientId: homelab_nifi
clientSecret: <redacted>
claimIdentifyingUser: email
admin: [email protected]
## Request additional scopes, for example profile
additionalScopes:
Additional example with custom keycloak install (provided by the chart maintainers)
After reviewing the User Management documentation:
- It may be necessary to pass in the ca cert for keycloak so that nifi has it in the keystore.
- There is also an option to use a central Certificate Authority (CA) will issue a Client PKI Certificate and Server Certificate for the Nifi server. This may be a valid strategy to trust the keycloak ssl cert because we can ensure they are generated by the same root CA.
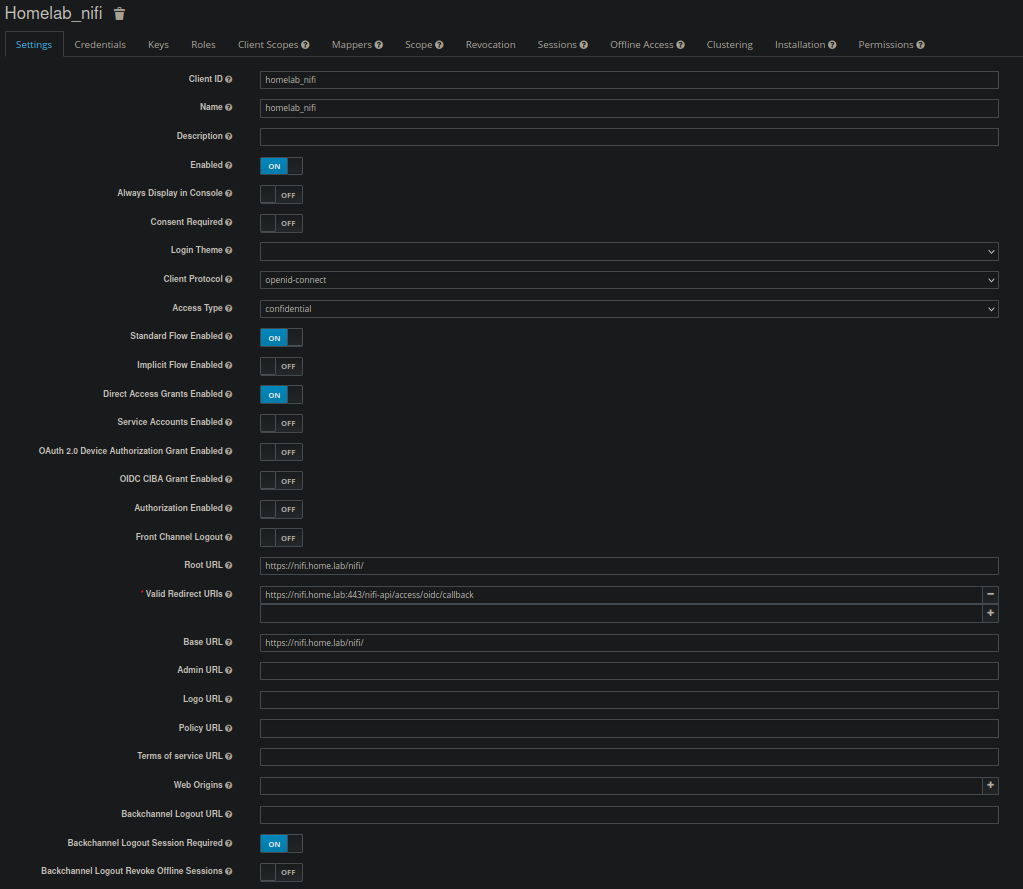
Keycloak Client Configuration¶
Create a new client for NiFi based on the following screenshots:
Troubleshooting¶
Valid Cert Error¶
Error Message:
PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
Possible solutions:
- https://docs.mend.io/en-US/bundle/wsk/page/how_to_resolve_error_message__pkix_path_building_failed__sun_security_provider_certpath_suncertpathbuilderexception__unable_to_find_valid_certification_path_to_requested_target_.html
- https://community.cloudera.com/t5/Support-Questions/Nifi-CLI-PKIX-path-building-failed/m-p/346504
Accepted Solution:
Create a ca.crt secret in the nifi namespace with the full keycloak cert chain:
Add the following configuration option to ensure the secret is added to the container:
Set the following configuration option to true. This ensures that the ca-secret that is created for keycloak is added to a new truststore.
Additional Resources¶
- https://github.com/sushilkm/nifi-chart
- https://github.com/ChrisEnglert/nifi-keycloak/
- https://quarkus.io/guides/security-openid-connect-web-authentication
Created : 28 avril 2023